NH man finds glitch in Google security matrix, (potentially) saves entire (Gmailing) world from scammers
If you are one of the 1.8 billion worldwide Gmail users, you can feel more secure knowing that Chris Plummer has your back.

MANCHESTER, NH – If you are one of the 1.8 billion worldwide Gmail users, you can feel more secure knowing that Chris Plummer has your back.
Last week Plummer of Manchester, who works in cybersecurity for a local medical system, caught something in his inbox that looked “phishy.”
What he did next will likely save millions of innocent people from falling prey financially to a sophisticated email scam that slipped through Google’s security safety net.
“It was midweek and I was going through my personal email as I usually do after work, and saw this message that appeared to come from a UPS email address,” says Plummer. “I’ve personally analyzed thousands of phishing emails and the most interesting aren’t the ones that get caught; it’s the ones that find their way into your inbox.”
In this case, the email looked unusually legit – it had what Plummer refers to as “Google’s stamp of approval,” a security feature the company launched last month as an extension of their Brand Indicators for Message Identification (BIMI) system.
The feature requires email senders to use authentication methods to verify their brand logo in order to display it in sent emails. As of May 3 Gmail users started to see a blue verification checkmark icon indicating that an email originated from a verified legitimate sender versus a scammer.
Although the email in Plummer’s inbox had the Google checkmark and a UPS logo, it was obviously sent from a scam account.
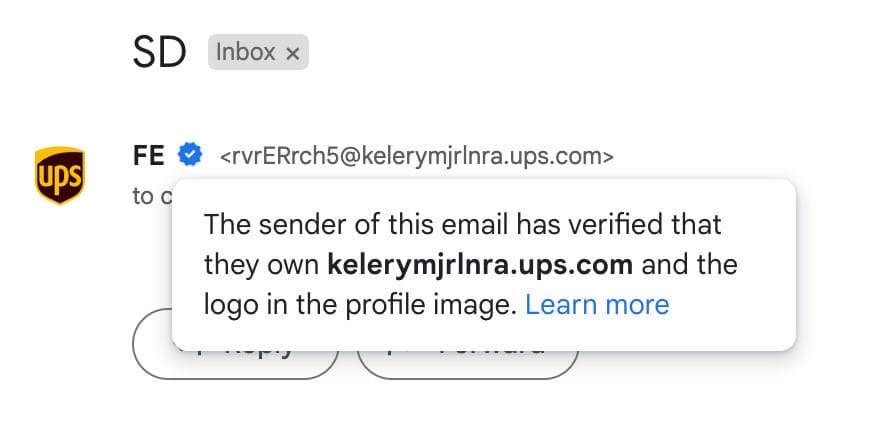
“This message was not passing tests for me personally. I could tell it was not legit but it was late at night and I had to run off to karate with my daughter,” says Plummer.
That was on May 30. The next day Plummer decided he would do the right thing and take advantage of Google’s bug reporting system.
“Not every company has one but Google does and you can follow the progress of those reported bugs if they get fixed. I submitted this and felt strongly about it. Google’s first response was that it wasn’t a bug,” says Plummer.
They quickly dismissed him. He could have shrugged it off.
“I chewed on that a little. When a big company like Google tells you you’re wrong it’s like they’re telling me I’m crazy. But I stuck to my guns and wrote an impassioned reply through their bug-tracking system,” Plummer says.
And then he did the other thing that can sometimes get you fast – and viral – results: He Tweeted about it.
“One thing I know to do is to at least share something like this on social media, and specifically Twitter has a thriving community of cybersecurity people,” Plummer says.
If anyone would “get” his sense of urgency over finding a glitch in the Google matrix it would be his techie Twitter tribe.
“The important part about this whole thing is that people using Gmail need to know this is a thing,” says Plummer. “My job is all about trying to protect vulnerable people and in this instance, everyone is vulnerable – whether you’re a cybersecurity expert or someone’s grandmother.”
Plummer dropped the following Tweet and then went to bed:
There is most certainly a bug in Gmail being exploited by scammers to pull this off, so I submitted a bug which @google lazily closed as “won’t fix – intended behavior”. How is a scammer impersonating @UPS in such a convincing way “intended”. pic.twitter.com/soMq7KraHm
— plum (@chrisplummer) June 1, 2023
“By the time I woke up it had one-hundred-thousand-plus views. I’ve never had anything like that happen to me. For some, that’s table stakes. Me? I’m just a guy from New Hampshire but I felt strongly that I was right, even after Google told me I was wrong,” Plummer says.
Hitting the amplify button on Twitter seemed to do the trick. A mea culpa quickly followed from Google.
“I had someone from Google reach out and basically they said ‘hey I think we got this wrong.’ I guess they wanted me to feel better that they were going to make it right – and they did. They posted a reply in their online tracking system to my report, so that was big,” Plummer says.
Google’s statement below:
After taking a closer look we realized that this indeed doesn’t seem like a generic SPF vulnerability. Thus we are reopening this and the appropriate team is taking a closer look at what is going on. We apologize again for the confusion and we understand our initial response might have been frustrating, thank you so much for pressing on for us to take a closer look at this!
We’ll keep you posted with our assessment and the direction that this issue takes.
Regards, Google Security Team”
Then, things got bigger.
“Friday night, in the middle of making dinner my LinkedIn started to blow up, which is weird for a Friday night. There was some French language conversation about this on LinkedIn, and with my three years of high school French, although terrible, I thought what I was reading was that UPS took an action on their own to get ahead of this issue,” Plummer says.
When he formally translated the post he learned that UPS in fact made changes to its infrastructure to help stop this scam from happening – because of his report.
“That is unbelievable – the kind of changes for a company of that size to have to make in such a short period of time? That’s an all-hands-on-deck kind of situation. I couldn’t believe the research I did compelled a company like UPS to change its infrastructure and actually got Google interested in changing its product,” Plummer says.
On Saturday Forbes published a story by tech writer Gordon Kelly about Google’s security warning, with great credit to Plummer for sounding the alarm. Wrote Gordon,
Plummer highlights that Google has now listed the flaw as a ‘P1’ (top priority) fix, which is currently “in progress.”
Immense credit goes to Plummer, not just for his discovery, but for the lengths he went to to make Google acknowledge the problem. That said, until Google has a fix, the Gmail checkmark verification system remains broken and is being used by hackers and spammers to trick you with the exact thing it was meant to combat. Stay vigilant.
“The scale of it is staggering – I almost can’t believe I’m the one who found this thing, and it’s real. The whole thing has been crazy,” said Plummer.
Plummer used the word “catastrophe” in describing Google’s security lapse in that the way it was set up, Google was, in essence, adding blue checkmarks and company verification icons programmatically.
“It’s a catastrophe because as an email user you’ve completely bought into this being a legitimate sender and may be far more inclined to act on anything they’re compelling you to do, whether it’s a phone call, or clicking a link and then getting into this ‘you owe us money for some shipment gone awry’ scenario. From there it goes in so many different directions,” Plummer says.
“The thing about phishing is that – it’s phishing. It’s a game of chance for criminals. The net is so wide that potentially 1.8 billion people could be reached, and there are economies of scale here. Does it take any more work to send to 20 people than to 20 million? Not exponentially. Some of us may put on the brakes, but it doesn’t matter. By the numbers, it’s going to pay off.”
He says Google missed the issue because their approach to applying a seal of approval relies on a number of standards which are imperfect.
“What’s more confusing to me is why Google would get into the business of certifying email. It was interesting that they were so bold in putting their own name on some of these communications when it relies on imperfect standards that are not within Google’s control,” Plummer says.
With the rise of ChatGPT and other AI technology, it could simply be that the competitive nature among the leaders in tech exerts pressure to roll out innovations before they’re completely debugged.

“All I know is they’ve assigned a priority and severity to it, actually priority and severity 1, which reads to me like one of the most important things they could be working on right now, so that’s something,” Plummer says.
Through his work, he is part of a group of cybersecurity experts from various sectors around the state who meet monthly to look at the various scams that are prevalent – right now Plummer says “romance scams” are hitting people hard because they take advantage of a person’s emotions on the way to taking their money.
In the end the takeaway for the 1.8 billion Gmail users out there is be vigilant – unless you’re also a cybersecurity expert, then also sound an alarm that leads to higher security an potentially saves email users around the world from getting scammed.
“Vigilance is the most important thing. You need to verify through some other channel when you get an email with a call to action – if they are prompting you to make a phone call, it should be to a number you already have. Email is decades old and this is still where we’re at. There really is no better advice than there was 20 years ago,” Plummer says.